Windows End of Support: Experts Unveil Risks & Implications
Why an unsupported Windows version could be your downfall
- End-of-support is a term used to describe when a product reaches its sunset date.
- This means that no new security updates or patches will be provided by the vendor after this date.
- We explore the implications of continued use of unsupported Windows OSes and paint the bigger picture in this article.
Ignorance is one of the biggest reasons people are victims of malicious attacks. Not being aware or motivated enough to protect your information. There is a need for improved public awareness of what they could be vulnerable to and how to prevent them from coming to fruition.
While Microsoft has done a good job of patching vulnerabilities with each new release, many organizations are still running older versions of Windows which have already reached their end of support.
For instance, Windows 7, 8, 8.1, and 10 continue to be used. This is even though they reached their end of support in 2020, 2016, and 2023 respectively. Windows 10 is safe, as support is ongoing until October 2025.
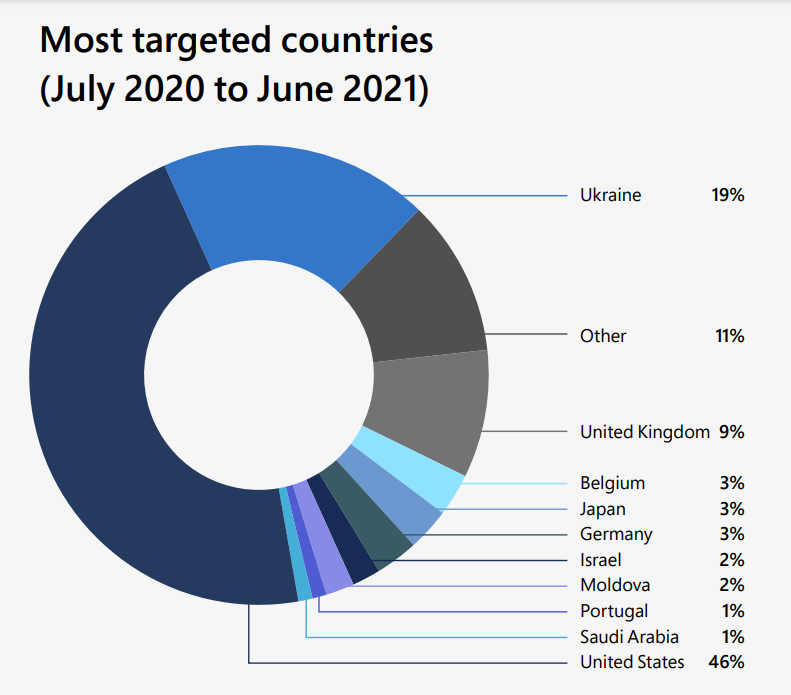
Because of their widespread use, Windows systems are at the top of the vulnerability list. When writing this article, Windows 10 adoption stands at a whopping 71%. This is more than half of the market share.
A single exploited vulnerability can lead to multiple infected machines and data loss, which can seriously threaten individual users and the entire organization they belong to.
This doesn’t have to be you. You can take charge now and prevent becoming another statistic of a compromised system. In this article, we bring expert opinions to shed more light on this matter.
What are the risks of using unsupported Windows versions?
Cyber threats are increasing in frequency and severity. They are also becoming more sophisticated and targeted. This is evidenced by the recent spate of ransomware attacks that have hit large organizations and small businesses. Most notably, DEV-0586.
In the world of computers and software, there are two main types of users: those who are tech-savvy and those who aren’t.
The former group, they know that Windows is a great OS. It isn’t perfect, but as long as you’re happy with its performance, your version doesn’t matter.
For the latter group, it can be difficult to understand why anyone would choose not to use the latest version of Windows.
If you have been following the news for the past few years, you may have heard about several major security breaches that have affected millions worldwide.
What these breaches have in common is that they were all caused by computers running an unsupported version of Windows.
And while hackers have carried out some of these hacks, others were caused by human error. Businesses should not be running an unsupported operating system. This is especially true if they want to protect their data and keep customers’ information safe.
As the expert Igal Flegmann, Co-Founder & CEO at Keytos reiterates:
Having security education in your organization is also very important so users do not click phishing emails and report attacks to your security team.

CEO at Keytos
Suppose you’re not conversant with the severity of the risk associated with running a version of Windows that has already reached its end of support, especially for a business. In that case, we break it down for you.
Security risks
It’s been reiterated over and over how running an unsupported OS is detrimental to your security. But just how dire are the risks?
The most important reason you should upgrade from an unsupported version is that Microsoft will no longer release security updates for these versions.
Unsupported software leaves your sensitive data vulnerable to attack by hackers. They can easily search for vulnerable systems that have not been patched.
According to experts, phishing is the most common entry point. Therefore, setting up Windows 11 MFA will go a long way in thwarting these attempts.
This is just the start. You will need more security solutions such that if one fails, your system will still be secure. Depending on one is suicidal because you risk losing your data if it is compromised.
In Joe Stocker’s expert opinion, Founder and CEO of Patriot Consulting and Microsoft MVP:
No security solution is perfect. It is important to have a layered security approach that includes a combination of technical and non-technical controls.

CEO of Patriot Consulting
and Microsoft MVP
And while all system controls may be in place, we cannot afford to ignore the role users have to play.
Staying up-to-date and installing security software is just the tip of the iceberg.
You also need to stay vigilant and have the ability to decipher an attack from miles away.
Otherwise, it’s just like having strong metal gates for protection but forgetting to lock them.
But this is not the only worry when it comes to obsolete OSes.
System failures
If your company is running an unsupported OS, you risk experiencing a system failure when a new vulnerability is discovered.
This could result in loss of data or downtime for your business operations. If you cannot quickly remedy the situation by patching the affected systems, new malware will proliferate throughout your network.
According to Joe Stocker:
Keeping devices patched, and using AV and EDR will reduce the exposure and risk for malware to run on an endpoint.Windows ASR, Applocker, WDAC, or Windows 11 22H2 “Smart App Control” can further reduce the risk of malware.
As seen from the effects of the DEV-0586 security vulnerability, it resides in the system drive and has the power to overwrite the Master Boot Record.
The MBR is the first sector of a hard drive, and it contains information about how to launch and run the operating system. When an MBR-based attack occurs, the bootloader’s ability to load the OS will be compromised, and the computer might not be able to start up normally.
This is why Chris Karel, Security Operations Manager for Infinite Campus recommends that you:
Have consistent backups that can’t easily be deleted or destroyed. And regularly test them to make sure they work, and cover what you need.

Manager, Infinite Campus
Performance issues
The performance of older versions of Windows becomes worse over time. This is because newer hardware requires more resources from an operating system than older hardware.
For example, if you install a new graphics card in your PC that supports DirectX but you’re still running an old version of Windows that doesn’t support these new APIs yet, games may run much slower than they would if you were running a newer version of Windows.
Many applications require specific versions of Windows to run properly, so if an application isn’t compatible with your current version, it may not work properly or at all. This could cause issues for users and IT administrators, who must find workarounds for these compatibility issues.
Chris believes that the only solution is:
Keeping systems patched and up to date. Both the operating systems (Windows, Linux) and the software that runs on it. (Exchange, web browsers, firewalls, etc) Especially with anything exposed to the Internet.
Essential Windows hardening techniques
Hardening refers to the process of making systems more secure. It’s an important step in the overall security process because it helps prevent unauthorized access, unapproved modification, and other attacks on systems and data.
Some of the hardening techniques you can employ include:
System configuration
The standard system configuration is often not secure enough to withstand a determined attacker. You can configure your system to be more secure by changing default configurations, setting up firewalls, and installing antivirus software.
The following are some important steps that can be taken to configure your system:
- Changing default passwords – By default many operating systems have a default password. If someone gets hold of your computer, they can log into it using this default password.
- Disabling unneeded services/applications – This reduces resource usage (memory and CPU), thus improving the performance of your machine.
- Setting up system policies – Policies help in configuring an organization’s systems according to specific requirements. The main objective behind using these policies is to ensure that all systems are set up so that they can be accessed by authorized personnel only.
After all, Igal reiterates that:
The best way to protect organizations in this zero-trust world is by reducing the surface area and removing the security responsibility from the average end user.
User access controls
User access controls are the first line of defense against attacks and should be implemented to prevent unauthorized access to systems.
The idea behind UAC is simple. Before running an application downloaded from the Internet or received in an email, Windows asks the user if this action should be allowed.
This means that if someone tries to install malicious software on your computer, they will need physical access to your PC and must manually approve each installation step. It makes it much more difficult for them to infect your computer without your knowledge.
We’ve seen some users disabling the UAC prompt because it is invasive every time you try to run an app, but it is obvious they haven’t thought about its repercussions. The good news is that Microsoft has made strides in ensuring this is something you can control.
You can use Windows’ built-in User Account Control (UAC) feature to help keep malware and other malicious programs from running on your computer. It is enabled by default, but you can adjust its settings to customize how it works.
Network security
The security of all systems within an organization is of paramount importance. However, network security is critical as it provides the mechanisms to protect other systems from attack.
This broad term encompasses a collection of techniques, processes, and technologies used to secure computer networks and their systems and devices.
Network security aims to protect information from unauthorized access or disclosure. This is done by using a combination of hardware and software to enforce rules that users, administrators, and programs on the network must follow.
These rules typically include authentication, authorization, encryption, and audit trail. To start off, you’ll need to install a firewall. Firewalls are one of the most important network security tools.
They can be software or hardware devices that control access to a network or a computer, providing a layer of protection from the Internet or other untrusted networks.
Another tool you’ll need is a VPN (virtual private network). This encrypted connection allows you to connect securely to an external server for remote access to your internal network.
The main reason why VPNs are considered a Windows hardening technique is that they can provide additional security when combined with other technologies like firewalls and intrusion detection systems.
They use encryption and authentication techniques to ensure that all traffic is secure. This makes it much more difficult for an attacker to gain access to your system to steal or damage information.
In addition to the traditional network security mechanisms, several new technologies that extend beyond traditional network security measures are emerging today. These include cloud computing and virtualization software.
Your network security system needs to be comprehensive, diverse, and flexible to adequately respond to the dynamic needs of today’s technology trends.
Application hardening
Application hardening is a set of best practices that improve the security of your applications. It’s not just about ensuring your system is secure but also that the services that run on it are secure.
It involves systematic processes and procedures to ensure that applications are secure and resilient to attacks. This is one of the most effective ways of reducing the surface area for vulnerabilities in your applications.
Shiva Shantar, Co-Founder and CTO for ConnectSecure believes that:
Weak passwords, outdated protocols, and unpatched systems in combination with untrained staff that click on malicious links are the reason for the vulnerability to spread.

and CTO, ConnectSecure
In other words, the security expert implies that the risk of vulnerability exploitation lies in a combination of factors.
It’s easily understandable why there is a need for a widespread security policy across the organization.
Not only do the decision-makers have to be involved, but all the users have to be educated about preserving security.
However, this is not too complicated if you apply a rigorous plan of action.
Here are some recommendations that organizations can implement to strengthen their Windows systems against potential threats:
- Keep your system up to date with patches.
- Install a firewall, antivirus software, and a good backup solution to protect your data and systems.
- Use complex passwords and change them regularly, at least every 90 days.
- Where possible, enable two-factor or multi-factor authentication for Microsoft accounts and other services.
- Use a password manager to generate, store, and manage complex passwords.
While you can implement all the Windows hardening techniques possible, recovery is critical to the security process. A recovery plan ensures the company can bounce back from a breach quickly and efficiently.
As a safety net, ensure you also run tests periodically on this plan to ensure it works as needed.
Igal emphasizes the importance of a recovery plan:
While prevention is paramount, having a strong recovery plan that gets tested periodically is also a key component of any cybersecurity plan.
Continuous vulnerability management
Continuous vulnerability management is a proactive approach to security that helps organizations avoid security breaches by proactively monitoring for emerging threats. The goal of continuous vulnerability management is to prevent cyberattacks before they occur.
Vulnerabilities can occur anywhere in your network, from your firewall to your web server. Since there exist many different types of vulnerabilities, you should also employ different systems to detect them.
As the threat landscape continues to evolve, so must your security strategy. It’s not a question of if your organization will be breached, it’s a matter of when.
The basic components of a vulnerability management program include:
- Identification – Gathering information about potential threats and weaknesses in an organization’s systems or networks that could be exploited by those threats.
- Analysis – Examining technical details about each identified threat to determine whether it represents a real risk to an organization or not.
- Prioritization – Ranking identified threats according to their severity or likelihood of occurrence. This is done to allocate scarce resources to those that pose the greatest risk to the organization.
- Remediation – Implementing controls to eliminate or reduce risks posed by identified vulnerabilities.
Igal raises awareness on cybersecurity:
Cybersecurity is unfortunately expensive in both time and money. But it’s important, so I’d also recommend that companies take it seriously and employ staff focused on security.
Vulnerability scanning
This is a process in which the security of a system or network is checked for any loopholes or vulnerabilities. Vulnerability scanning helps identify any flaws in the system and advises on how to fix them.
Organizations can ensure that their systems remain secure from malicious attacks by having a vulnerability scanner in place.
Patch management
This is another process that is important for maintaining a secure environment. It involves installing patches for known bugs and vulnerabilities in software applications or operating systems.
![Your PC Won't be Entitled to Updates: How to Bypass [100% Safe]](https://cdn.windowsreport.com/wp-content/uploads/2022/04/check-for-updates-5.png)
It ensures that all systems remain up-to-date with the latest technology updates and that any vulnerabilities are resolved before hackers exploit them.
Incident response
This refers to responding to and recovering from cyber attacks within an organization’s network or system.
Incident response is essential because it helps organizations recover from cyberattacks quickly and efficiently. All this is done while preventing further damage to their systems by hackers, such as ransomware outbreaks or data breaches that could potentially lead to financial losses due to data theft.
Secure Coding Practices
Secure coding practices are a set of coding guidelines that help programmers write more secure code. It is important to note that secure coding is not about preventing all vulnerabilities.
Instead, it focuses on reducing the risk of introducing new vulnerabilities and the impact when vulnerabilities are exploited.
Here are some ways in which secure coding practices can mitigate Windows vulnerabilities:
- Secure code review – A secure code review involves reviewing source code for potential security issues before the product is released into production. This helps identify potential problems before they become an issue, thus reducing the likelihood of future attacks against these products.
- Test-driven development – Test-driven development (TDD) is a software development process that ensures each unit has been tested thoroughly before being integrated with others and deployed into production environments, thereby minimizing errors due to integration issues at later stages.
Adhering to coding standards is not just about making your code more readable for others; it also helps you write fewer bugs and spend less time maintaining your codebase over time.
Shiva’s sentiments on the issue remains:
Secure coding is not a good practice but a mandatory one.
Cybersecurity education and awareness
Cybersecurity has become a top concern for all organizations — from small businesses to large enterprises — in recent years.
Cyberattacks are increasing in frequency and sophistication, making it more important than ever for companies to have good cyber security tools in place. And while most businesses recognize this need, many don’t know where to begin when it comes to addressing it.
A comprehensive cybersecurity education program can help solve this problem by providing employees with the knowledge they need to identify potential threats, understand how these threats could impact them and their company, and know how best to respond when an attack occurs.
This type of education also helps align employee behavior with company policies related to cybersecurity compliance and risk management.
In addition, cybersecurity education helps reduce costs associated with breaches by increasing the likelihood of identifying and containing them early in their lifecycle.
One of the most effective ways to mitigate risk and prevent security incidents is by promoting a culture of security awareness. This involves empowering your employees to proactively identify and report potential security threats promptly.
There are different ways you can go about achieving this:
- Reporting mechanisms – Create a dedicated internal network for reporting suspected incidents. This should be separate from your corporate network so it doesn’t create a single point of failure for the organization.
- Employee empowerment – Train employees on identifying suspicious emails or websites and reporting them if they notice anything unusual.
- Security training cannot be a one-off event – Security training has to be repeated regularly so that people keep up with new threats and risks that emerge over time.
Conclusion
As more and more organizations downplay the significance of Windows end support, their network and technology risk exposure increases. Fierce attacks that abuse security features in unsupported devices or operating systems have become a high probability.
What is clear from the various risk scenarios here is that the only sure way to safeguard your organization from increasing digital risks is to migrate from legacy Windows OS, critical applications, and systems to supported Microsoft solutions now rather than later.
One thing is for sure. If you’re running a business, you need to take heed of the computing and security changes happening right now. We’ve discussed how upgrading an operating system can pose hidden dangers and the significant costs of neglecting to upgrade.
The rest is up to you to ensure you implement them. Regarding using unsupported OS, taking them off the network is best for you. If it’s absolutely necessary to use them, ensure they’re safely tucked away from online risks.
That was quite a mouthful, but we hope it has been an insightful session and you now understand the implications of stagnating on unsupported Windows versions.
Is your organization up-to-date with your OS? What steps have you picked up from this article that could steer you in the right direction of securing your systems? Let us know in the comment section.